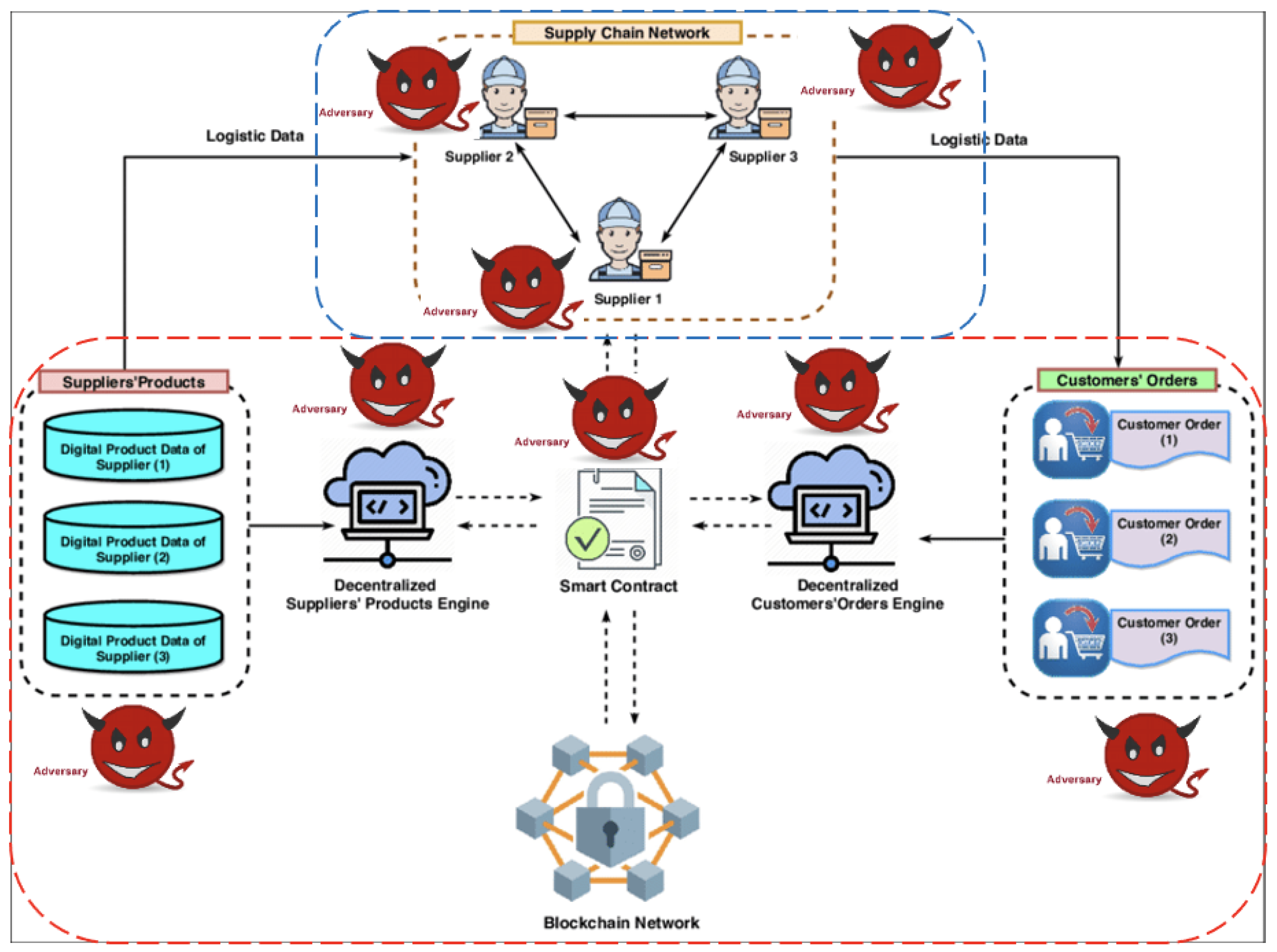
Machines | Free Full-Text | Securing Blockchain-Based Supply Chain Workflow against Internal and External Attacks

A Mechanism to Detect and Prevent Ethereum Blockchain Smart Contract Reentrancy Attacks | Semantic Scholar

Explain in detail the security vulnerabilities of Ethereum smart contracts, how to effectively reduce DeFi attacks? – Blockcast.cc- News on Blockchain, DLT, Cryptocurrency
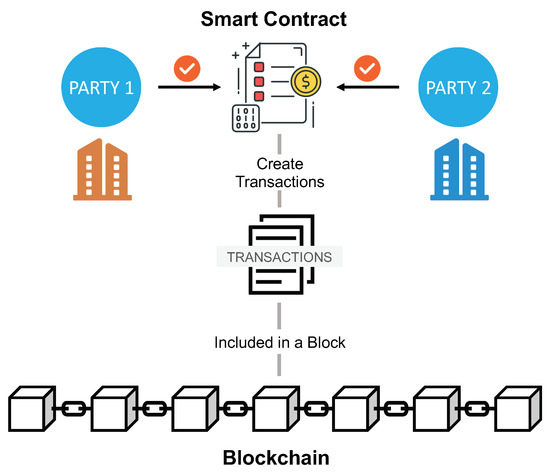
Future Internet | Free Full-Text | Toward Vulnerability Detection for Ethereum Smart Contracts Using Graph-Matching Network
![All About Smart Contract Auditing - Denial Of Service Attacks On Smart Contracts [2020] - Blockchain Application Development - Somish Blockchain Solutions All About Smart Contract Auditing - Denial Of Service Attacks On Smart Contracts [2020] - Blockchain Application Development - Somish Blockchain Solutions](https://i.ytimg.com/vi/wkKaA8sQA7I/maxresdefault.jpg)
All About Smart Contract Auditing - Denial Of Service Attacks On Smart Contracts [2020] - Blockchain Application Development - Somish Blockchain Solutions

Smart Contract Security – Expect and Deal with Attacks - Trust & Security in the Blockchain - Blockchain & E-Government - Issues - dotmagazine

The number of attacks from smart contracts accounts for a significant... | Download Scientific Diagram

The number of attacks from smart contracts accounts for a significant... | Download Scientific Diagram




![PDF] Smart Contract: Attacks and Protections | Semantic Scholar PDF] Smart Contract: Attacks and Protections | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5d30af04fa41ed28d91c621ab51c6f83d9df3296/5-Figure3-1.png)
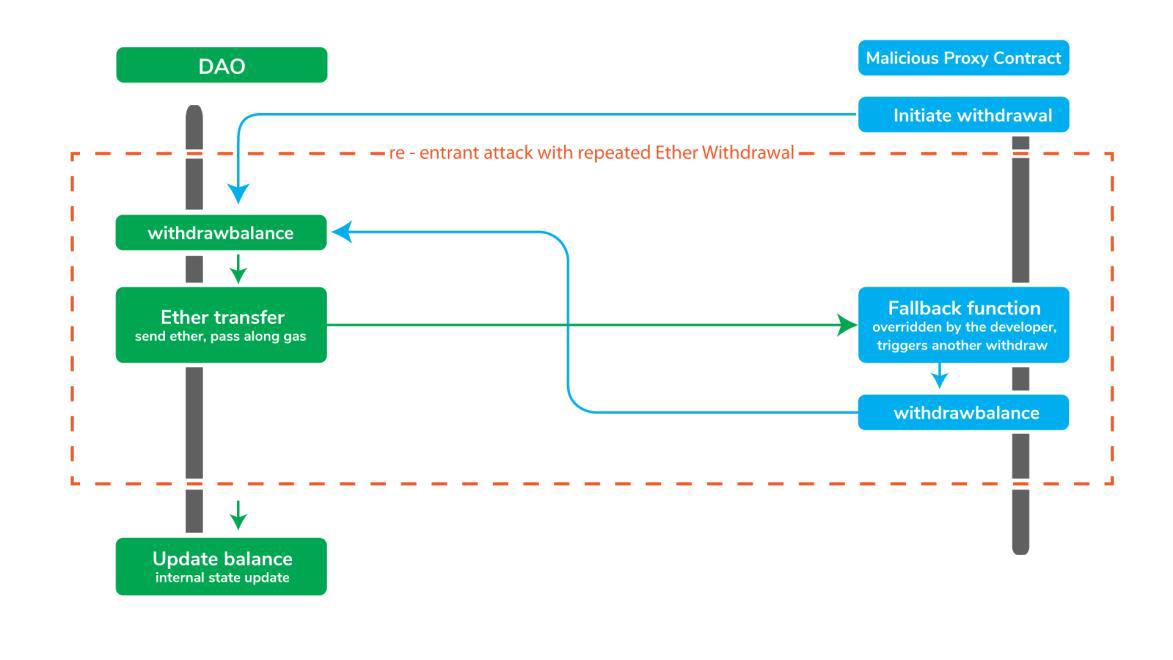
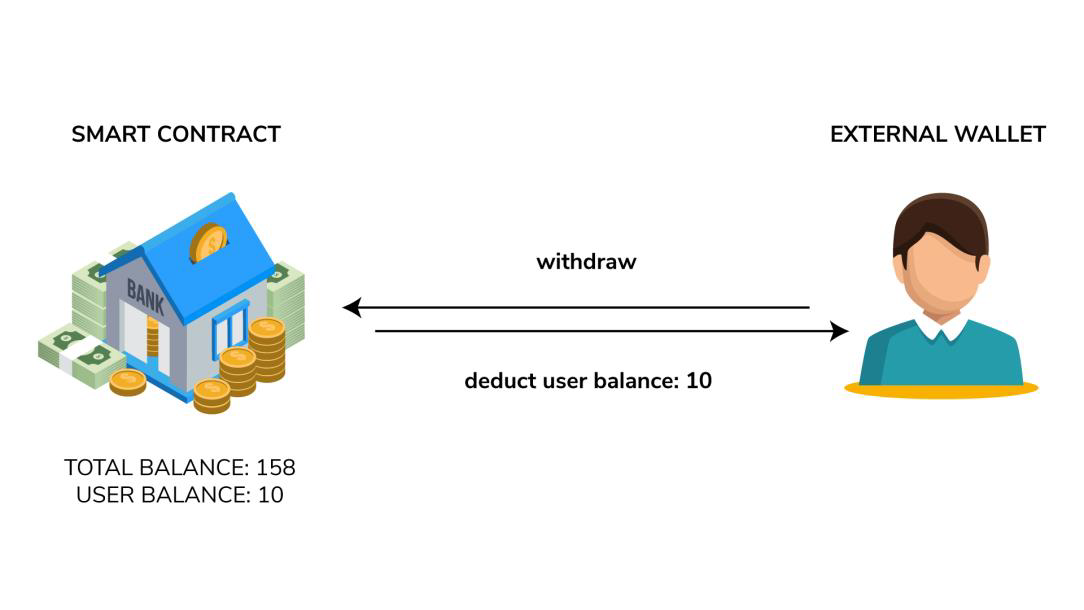




![Smart Contract Attacks [Part 1] - 3 Attacks We Should All Learn From The DAO | HackerNoon Smart Contract Attacks [Part 1] - 3 Attacks We Should All Learn From The DAO | HackerNoon](https://hackernoon.com/hn-images/1*UeDgMZo2n0skHzgkl352zQ.png)




